Succesfully deploy your Data Strategy
To support the business strategy, all employees must have the right information available at the right time in the right place to perform their work effectively and efficiently.
All employees must therefore have simple and reliable access to the right applications and data via the available devices. There must also be a reliable and secure infrastructure that connects the devices, applications and data. The data strategy must therefore connect seamlessly with the IT strategy and the business strategy. The same, of course, applies to data, IT and business architecture.
Emerging technologies enable a new generation of data management skills. These make it possible to integrate and implement the strategy for defensive and offensive data. It is essential for any business to strategically manage data and information. Companies that have not yet developed a data strategy and solid data management must either catch up quickly or prepare for exit.
A data strategy can be effectively deployed based on the synergy between the following components:
- Data Awareness,
- Employee empowerment,
- Processes that ensure access to high quality data,
- Technological requirements for storage, sharing and analysing data.
Please click on this link to do a quick assessment of the current data strategy implementation before you continue reading.
Data Awareness
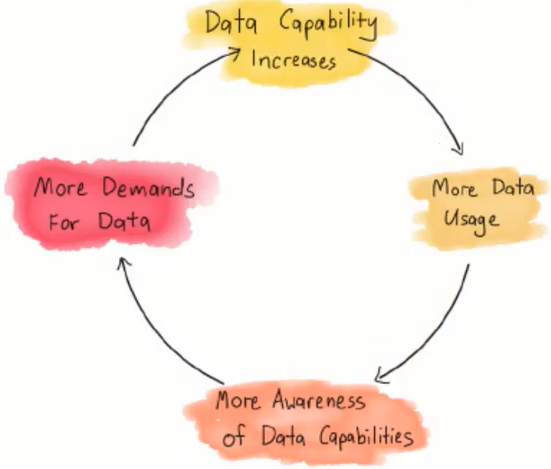
An organization that has made the choice to work data-driven will also have to ensure that employees at all levels are data-aware. This can be achieved by making employees familiar and creative with the possibilities that arise for the activities of the employee through the use of data as a digital asset.
It is important to note that a successful data strategy will lead to optimal use of data while developing an increasing need for more data. This is because employees are stimulated in their creativity and discover more possibilities to use data effectively for innovations and optimization of their department and the company as a whole.
Giving examples is part of this awareness campaign and these must be in line with the chosen business strategy. A concrete example has been elaborated in the material tab of this chapter to indicate the effect of a good data strategy.
Employee empowerment
Providing your employees the right tools, applications and data is a good start but not sufficient when the organisation is moving towards a data driven business model. Remember one of the characteristis of the data driven platform model is the holacratic organisation.
A holacratic organization is built around autonomously operating cells, the so-called holos. Working in a holos requires that the employees are able to achieve optimal collaboration and productivity with minimal hierarchical structures, which is also perfectly aligned with the other parts and facilities of the platform of which the holos is part.
The HR department responsible for the knowledge, skills and competences of employees will therefore have to investigate, record and optimize how employees are able and enabled to function well in this model. This will lead to higher employee satisfaction and loyalty.
It implicates that employees will more often be able and willing to make independent decisions on the basis of the right data, knowledge and insights, instead of having to call in a manager for this. This improves the decisiveness of a department or company. At the same time employees must be aware of risks of their decisions and the responsibility they bear for them. In many organizations tasks, responsibilities and authorities are laid down in a framework with profiles. Extensions and adjustments will therefore be necessary.
As a direct result employees and managers no longer have to ask a specialist to compile a report, because these are immediately available with up-to-date data via self-service portals and dashboards. Those repetitive and boring tasks of a data expert can be replaced by, for example, developing the most desirable and optimal views and services in BI and AI tools. These expired and new tasks also require adjustments in job descriptions, rewards and work processes from both the user and the report creator.
Processes to support data strategy
As we make new tools available and create new insights, we also need to determine who has access to them, with what rights, and under what conditions. This means that the authorisation scheme must be checked and adjusted where necessary based on changed possibilities for existing employees. Of course, new employees and employees with a different role must also be included in the schedule.
Authorisation
We might already have established that people who log in are actually the ones they pretend to be. This can be done by means of identification, authentication and authorization. We briefly explain the differences:
- Identification of an employee consists of establishing the identity on the basis of a unique code, usually in combination with a password. The role of the person and the rights to the environment are linked to this code. The employee must be able to identify himself.
- Authentication prevents employees from consciously or unconsciously exchanging a code and password. We want to check whether the code is actually used by the right employee. This can be done by sending and verifying a one-time code via a mobile phone. There are also standard tools for authentication, their use simplifies the login process for the employee.
- Authorisation is the process that determines who has permission to access or use tools, applications and data. A system administrator defines which users can access the system, with what permissions, at what times, with how much storage, and so on.
Data Quality management
The use of data requires the right quality for specific purpose. The quality requirements may be different for different uses. Based on the data strategy, the use of data for new goals will be desirable and that is why we must also record the required quality for those goals. This means that we have to evaluate and adapt the existing criteria with which we determine quality for the new applications of data.
When determining the required value per criterion, we take into account the type of data, passive or active. We use active data to build up our digital assets. Statistics, historical overviews and static data use passive data. These are of great importance for the management and auditability of an organization.
Data quality management is a continuous process for monitoring and increasing the quality of data. It is advisable to select a suitable tool for this that monitors the data, metadata and master data. This process must be secured in data governance.
Masterdata management
When using data, it is important that we make it readable for both humans and machines. Since machines can only make binary decisions, any doubt about the authenticity of data must be excluded. We therefore describe data with sufficient metadata to make an object unique. We also use a data dictionary to ensure that everyone uses the language and the correct name in the correct context. The master data is important for this.
We explain the three data terms in a simple example of a school administration.
Data consists of the lines in a table. The columns contain the Metadata. For example, if the first column is a last name, followed by a first name, date of birth, student number, school year, and location. In this way, we make every student unique. Master data describes the syntax and appearances in each column. The same properties and requirements apply to each column.
Any system that manages master data will ask an administrator if a new appearance is acceptable and then make it a new column, or consider the appearance as wrong. As soon as a new date of birth is recorded it will be included in the master data, unless it is an impossible or unaccepted notation of a date of birth. Then there is an action that can consist of ignoring if the data quality is preserved or an intervention to guarantee the data quality.
In the picture you read the seven steps for master data management, starting with a vision. Especially the metrics should be aligned with the data quality criteria as mentioned above.
Data Governance
Just like the strategy and architecture, data governance is linked to the IT and Business version. Data Governance is therefore a derivative of Business and IT Governance and must fit in with the applicable rules, regulations, procedures and standing organization.
At the data level, governance must give substance to the protection and improvement of quality, safety, ethics and risk management. The data strategy requires that it is examined whether all rules, procedures, and applicable legislation are still current and relevant enough.
Moreover, we have already described that roles, rights and assignment to existing and new persons require attention, both from HR and from the governance structure.
Privacy and ethics
The data strategy can influence the use of data for new applications. It is therefore necessary to check whether the current rules for ethics are respected and whether they still provide sufficient ethical protection for customers, employees and the relationship maintained with them.
Traceability of persons on the basis of technically combinable characteristics is, for example, a violation of ethical rules and certainly of privacy. Anonymization of personal data alone is therefore not always sufficient.
Risk and compliance
It is becoming clear that the more and smarter use of data can also create risks for privacy, and also for business-critical information. We already mentioned this at the beginning of this training in “opportunities and threats” of data-driven working.
A lot of money is made in an illegal circuit where people focus on obtaining personal and business-critical information. Employees can be sensitive to approach by persons from the illegal circuit and it is a good idea to test employees for such announcements and to consider why employees would be sensitive to them.
Liability as an organization can increase due to new services and the use of external data sources for this.
The protection of these and other risk factors and the prevention of misuse must therefore be included in our risk analysis and mitigation. Of course, the same checks and adjustments apply to compliance with laws, rules and regulations. Are the current policies still sufficiently up-to-date and relevant or are adjustments required?
Technology to support data strategy
When developing the data strategy, we already stated that requirements must be included for the available technology. For a successful roll-out it is necessary that these requirements are met.
If there are still shortcomings, for example due to budgetary reasons or a lack of time and people to realize the adjustments, these are risks for the successful execution of the data strategy. It is recommended to prepare a risk analysis and a series of protective measures for the following items.
- Applications do have adequate reporting functions and easy access to actual, relevant, and high quality data,
- Tooling for dashboards and self-service portals are sourced, available, communicated, and explained to all users,
- User Devices are available and equipped to support acces to data, applications, and portals as mentioned above,
- Infrastructure is ready to support all connected devices, on all locations, for all authorised users.